Let’s do a thought experiment. You run an organization that sells smart irrigation monitors and other vital agricultural products and services; then, out of the blue, you’re served a ransomware message and your files are now encrypted and rendered useless.
How did this happen?? Luckily, you have a plan for this — a 5-year-old incident response plan left as a relic of your previous CISO. You begin to follow the plan, but begin to realize it’s now obsolete.
Your last backup is from a year ago and hasn’t been tested. You never thought you would need it.
That 5-year-old incident response plan and untested backup are a risk that’s being carried on your firm’s balance sheet — a bill that has come due in the form of a ransomware attack.
Ransomware demands now average $5.3 million, and in September, the FBI issued a warning that ransomware gangs were actively targeting the agricultural sector.
Cyber attacks on the agricultural industry are soaring because the food and agriculture industries have steadily increased their technology adoption that makes the most out of automation & data. While this makes daily life in the agricultural sector more productive & efficient, it also introduces new vulnerabilities as the attack surface expands.
The agriculture industry has embraced digitalization
The agriculture industry is transforming. Your farmer today is more technologically savvy than in the past. As a result, the agriculture industry actively embraces the IoT paradigm and adopts effective solutions to have a competitive edge. Digital solutions that increase their efficiency, their ability to undertake new contracts and grow, and make them leaner and meaner — cutting overhead and increasing productivity.
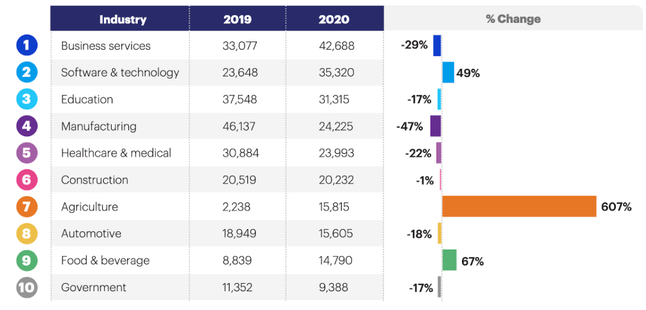
While increased modernization improves daily life for growers, it also expands their attack vectors and provides more endpoints for cybercriminals to infiltrate. For example, in 2020, ransomware attacks on the agriculture industry rose by 607%. To put that in perspective, the next largest change was the food & beverage industry, with a 67% increase.
Deploying ransomware is becoming even easier for cybercriminals as attacks are increasingly driven by Ransomware-as-a-Service (RaaS). The evolution of RaaS enables unsophisticated actors to pull off increasingly complex attacks by relying on established RaaS like REvil & BlackMatter.
Why do cyberattacks end up costing so much?
Ransomware attacks are low-risk crimes that can have a massive payoff because most cybercriminals live and operate in countries that condone their activities — they have a sort of blanket amnesty.
When cybercriminals attack, the cost is usually much higher than the ransom demand. Whether your organization decides to pay or not as you deal with the fallout of a ransomware attack, the costs start to add up.
Business continuity: The average ransomware attack takes up to 21 days to fix. Meanwhile, you have no revenue and costly expenses.
Class action lawsuit: Lax cybersecurity measures have cost companies millions in payouts to their clients and the people they serve. For example, Target had a $58 million class action suit due to an attack that compromised their consumers‘ data.
M&A: Mergers and acquisitions, as case studies have shown, can be ruined by cyber attacks. Cybercriminals are known to track M&A activities through publicly available information and will decide to strike when they are capable of doing the most damage. This will result in either the deal falling through or the price per share dipping.
Stock price: Bad press will affect your stock price and the value of your shares. An attack on your agriculture business will have an impact on your shareholders’ portfolios.
Consumer loyalty: Today, privacy is a big issue. Consumers take umbrage when they feel their company of choice has betrayed their trust in this regard — whether it was intentional or not.
What can you do to prevent an attack?
Change your posture
Most organizations react to cyberattacks. But the single most crucial step you can take is to make your security controls proactive. That means categorizing your organization’s risk and data to determine which pieces are the highest priority. Ultimately, helping you prioritize which risk to address first.
How do you take control of your organization’s cybersecurity risk?
Create an incident response plan
Eventually, your organization will be breached. It’s inevitable. The reality is that the biggest risk factor to your organization is the carbon-based lifeforms (humans) on your payroll. Accessing open WiFi, having simple passwords, not having the proper encryption on their phones — using tools that aren’t protected.
It’s important to acknowledge that you will get hit with an attack sooner or later. When that happens, you need a good incident response plan.
One that takes into account:
- How quickly do you recover
- If you have a recent backup
- If you’ve tested your backups
- How fast you patch the leak or breach
Supply chain security risks
It’s essential to understand the upstream and downstream impact that a ransomware attack on your organization could have. It’s not just your systems that are vulnerable, but all those in your supply chain that might get hit by an attack. If you’re breached, what kind of impact will it have on your customers?
In September 2021, New Cooperative, an Iowa agricultural supply chain involved in 40% of the nation’s grain production, was the victim of a ransomware attack by BlackMatter.
But you may remember BlackMatter better by their previous name – DarkSide.
That’s right, the same group that ransomed Colonial Pipeline and shut down 45% of the east coast’s fuel supply in May went on to impact 40% of the United States’ grain production.
Every organization absorbs the risk of all of those up and downstream from you.
It’s not uncommon for organizations to view cybersecurity as a check-the-box activity during leadership meetings. But that approach can lead to outdated and untested security controls – a bill your business is steadily accumulating that comes due when you’re breached.
Feel free to reach out to us via the form below for a free consultation to start shifting your organization’s security posture to proactive rather than reactive.
◅ SEE OUR SERVICES
Learn how our suite of capabilities fuels business innovation
GET IN TOUCH ▻
Talk to us about solving data-driven challenges with speed & scale
